How does the Guardian roof work
Where a glass or polycarbonate conservatory rooftop simply gives cover among you and the components, the Watchman Warm Rooftop accomplishes such a great deal more.
The plan of the strong Watchman traditional conservatories uk rooftop comprises of various layers of best in class protection. This implies that warm air can’t get away from in the colder months, keeping the conservatory hot inside.
In the mid year months, you don’t get the nursery impact of daylight spilling through glass and not having the option to get away. The Gatekeeper Warm Rooftop is strong – going about as an actual boundary to coordinate sunbeams from a higher place. It additionally has underlying ventilation to permit air to course, forestalling dampness developing and shape in the new rooftop.
Delightful conservatory rooftop wraps up
At the point when you supplant your conservatory rooftop with a Watchman rooftop you’re ready to browse different sharp, normal looking records or tiles for the outside. These quality materials give the completed conservatory an expert appearance very much like a full expansion, and you can pick tiles that match the variety and style of the remainder of your home.
So there’s compelling reason need to pick either conservatory or expansion – a conservatory transformation with a Watchman Warm Rooftop gives you both. What’s more, when you have another nursery room that is fit to live in, there are an entire scope of additional opportunities accessible to you.
A genuine additional room in your home this modest expansion arrangement revives an ignored room – giving you fundamentally more area than you naturally suspected you had initially. When you convert your conservatory you won’t have any desire to move house.
In any case, assuming that you could possibly do, your new nursery room will raise your home’s adaptability and worth.
A traditional conservatory garden room is just worth having on the off chance that you can invest energy serenely in it. This is unfortunately not the situation for polycarbonate and glass roofed centers because of the radical temperature changes.
A strong Gatekeeper Warm Rooftop changes the conservatory into a room like some other in the house, just with a quieting perspective on your nursery. Ideal for loosening up following a bustling day, or partaking in a calm end of the week in the regular light with a paper or a book.
A conservatory rooftop substitution from Ventures 4 Material meets all building guidelines fundamental for it to turn out to be very much like an expansion to your home. Consequently visitors can rest in the room for the time being, protected in the information that the construction is sound. The upsides of the strong rooftop likewise mean they’ll not be upset by downpour commotion, cold 12 PM blasts or blistering summer dawns.
Large numbers of our clients appreciate moving their eating table into their new changed over conservatory for a splendid, close outdoors climate.
An additional room in the house implies you can utilize it for almost anything you need. As you would with a typical expansion, the conservatory changes into a kids’ play region complete with Drove spotlights in the new roof. On the other hand, in the event that you believe a spot should escape from the children, put a flatscreen on the wall and partake in another television room or parlor.
Double-Entry Accounting in Modern Times
My Investor Arranged Monetary Bookkeeping Training Link (S-OFA) Norms will expect that charges equivalent credits.
Duh. In any case, in the event that I am really going to begin with a spotless piece of paper, then, at that point, I’m constrained to make sense of how twofold section bookkeeping fills a need. I see three potential avocations:
Mistake checking — However I expect we can promptly concur that the times of recording a number two times to confirm that the two numbers match are a distant memory.
Obstruction to fiscal report control — The essential thought is that a preliminary equilibrium resembles an inflatable loaded up with water: assuming you crush in one spot (e.g., income), some other spot will swell (e.g., records of sales).
Reasonable financial model of a business venture — The instructive worth of twofold section bookkeeping as monetary model would be the most convincing defense. I will make sense of that this way off the mark for being valid any longer.
How Twofold Passage Headed out in different directions from Financial aspects
In 1494, the Gutenberg print machine made it workable for Luca Pacioli, an Italian priest, to distribute an article of twofold section bookkeeping as worked on during his lifetime. Pacioli demonstrated the way that the cases on the resources of an undertaking can be no more, or no less, than the actual resources. Bookkeeping’s crucial characteristic, as he portrayed it, is the adherence to this permanent law of financial matters.
Pacioli likewise portrayed the overall view that cases on resources were dichotomous. In his fifteenth century world, a case could be either a responsibility or the proprietors’ value — not both. Likewise, the pay of the proprietors through the tasks of the endeavor could be gotten from the change during the period in net resources (gave that the resources and the liabilities were estimated accurately).
Throughout the hundreds of years since Pacioli distributed his course reading, a gap between twofold section bookkeeping and the genuine financial occasions influencing an endeavor has arisen:
A large number of resources are missing from monetary records, and estimation can be erratic.
The thought of a plainly obvious division of cases has been delivered shortsighted and futile by propels in monetary administration and other business improvements. (See my past post for a greater amount of my interpretation of this – and a development when I can carve out the opportunity.)
More subtle, however similarly as significant, is the shortfall of a correspondence among cases and resources. The FASB and each and every other surviving standard setter has taken on non-relating models for resource and responsibility acknowledgment (and estimation). Saving the unexpected issue that a few resources/liabilities perceived are not really resources/liabilities (e.g., conceded gains and misfortunes), the impact of two acknowledgment rules is to deliver monetary records for which the left-hand side shows a specific subset of financial resources; and the right-hand side shows an alternate subset of monetary cases.
Twofold passage bookkeeping actually guarantees that the accounting report adjusts, yet that reality doesn’t let you know a lot of anything any longer. Notwithstanding the absence of correspondence and the shortfall of numerous resources from the monetary record, we actually continue getting bookkeeping profit from changes in net resources. However, most importantly, in current twofold passage bookkeeping, there is no primary concern.
As I think about what all of this will mean for my investor arranged monetary bookkeeping framework, I see three ways:
Keep on shielding twofold section as a monetary model: that adjustments of net resources is a sensible portrayal of financial profit — I don’t trust this briefly.
Imagine another meaning of profit that doesn’t sensibly rely upon changes in resources and liabilities — Regardless of whether a chance, it will not occur at any point in the near future.
Recognize that twofold passage bookkeeping is no longer something besides a gadget for beating fiscal summary control down — and act as needs be.
Subsequent stages
By ‘act in like manner,’ here are a few instances of my arrangements:
Truth in marking — Beginning with a spotless sheet ought to likewise mean discarding such old phrasing as “profit” and “monetary position” that have come to guarantee beyond what they can convey. There could have been a period some time in the past while bookkeeping verged on estimating monetary profit and monetary position, yet not any longer, and probably at absolutely no point in the future.
Accommodate, accommodate — The property of twofold passage bookkeeping that thoroughly connects stocks to streams (i.e., “explanation”) will be taken advantage of to the greatest degree practicable through definite quantitative revelations that are connected straightforwardly and expressly to the budget reports, and among themselves.
Relating acknowledgment standards — In spite of the fact that I can’t express this without a doubt, that wouldn’t shock me at all assuming Pacioli had understood that a case on one substance should likewise be a resource of another element (to a greater degree toward that in a subsequent post). Consequently, a non-comparing definition for liabilities, and other non-remaining cases, isn’t required. Everything necessary is a meaning of “resource” for bookkeeping.
Claims show — Rather than liabilities versus proprietors’ value, S-OFA will allude to ‘non-remaining interests’ versus ‘the leftover interest’ (the last option being estimated as the contrast between all out resources and all out non-lingering interests). Hence, the inquiry that has beset the FASB of what is a risk, or what isn’t, will boil down to an issue of show. For instance, unadulterated liabilities might be introduced collectively, aside from the mixture claims I referenced before.
How to Organize Every Room of the House with Plastic Storage Bins
Today we are discussing one of my exceptionally most loved things-capacity plastic storage boxes! I’m a smidge fixated on them and use them all around my home to sort out everything!
Presently, having pretty, matching receptacles doesn’t be guaranteed to approach association. (Nor doesn’t having pretty, matching receptacles fundamentally equivalent disorder.) Notwithstanding, I love that a ton of these choices can assist with enlivening a space while keeping up with some similarity to arrange simultaneously when utilized really, and practical + wonderful is dependably a success in my book!
Coordinated storage space with emptied baking things, pasta, and flavors
Snatch our free getting sorted out guide, 7 Basic Beginning stages!
This fast aide gives you 7 straightforward, commonsense ways of starting to handle a staggering getting sorted out project. (Furthermore, when you get everything rolling, the energy will assist you with continuing onward until it’s finished!)
Instructions to Coordinate Each Room of the House with Capacity Containers
This post contains member joins. For more data, see my divulgences here.
Since I realize that large numbers of you share my affection for capacity holders, I figured I would share a rundown of my #1 kinds and how I use them on the off chance that you have any impending association projects underway! In no specific request, here are the kinds of capacity receptacles I utilize most frequently:
1. Containers
I love bushels since they come in so many various shapes and sizes and can add warmth and surface to a room while keeping things perfect and clean. We use containers in a few spots in our home, remembering for my office to store texture, make supplies, and little stylistic layout pieces…
IKEA BESTA Stockpiling Unit with Capacity Crates for Association, Stockpiling Containers
crates (comparative) holding everything from texture to create supplies to style things
…in our kitchen cupboards to hold little utensils that we really want, yet aren’t utilized constantly…
Coordinated Kitchen Cupboard, Utilizing a Wicker Stockpiling Bushel to Hold Additional Utensils that Are Required however Not Utilized Frequently
utensil container in our kitchen
…furthermore, in our lord storeroom to hold additional toiletry things, nail clean, belts, and the sky is the limit from there.
Coordinated Expert Storeroom with Capacity Containers, Stockpiles Receptacles, and Capacity Sacks
2. Texture Canisters
I use texture containers constantly, especially in our “cubed” capacity units. I love that they come in lots of various varieties and are sufficiently large to hold a great deal of little things, yet little enough to hold a region back from getting jumbled.
So I frequently will add a glue bookplate to the front of my texture receptacles so I can embed a name and obviously see what is in every one.
IKEA KALLAX Stockpiling Unit for Toy Association, and Texture Receptacles with Bookplate Names
texture receptacles (comparable) with bookplates keeping the Cs’ toys coordinated
You may likewise have detected the round texture capacity receptacle in the photograph above, which is ideal for arranging taller things! We use it for Nerf firearms in the den, I’ve utilized it to coordinate rolls of wrapping paper, and it likewise makes an extraordinary clothing hamper!
Coordinated Enclosing Paper by a Round Texture Stockpiling Receptacle
Another sort of texture container that I love to utilize are texture totes. HomeGoods/TJ Maxx generally convey a lot of these in different sizes and varieties, and I have utilized them to store everything from sweaters to swimming outfits to grips and wallets.
Texture Capacity Sacks in a Coordinated Expert Wardrobe
3. Plastic/Acrylic Stockpiling Drawers
I once saw plastic drawers on a rundown of “things you ought to never use to coordinate,” and I thoroughly conflict! I love them!
Not at all like plastic tubs that you need to unstack each time you need to utilize their items, drawers are effectively open when stacked and are ideal for sorting out things under the sink, cosmetics, composing utensils and office supplies, toys, little storage space things and more.They are likewise simple to mark, which is generally an or more!
Acrylic Stacking Stockpiling Drawers Used to Sort out the Region Under the Kitchen Sink
acrylic capacity drawers marked with glue vinyl phrasing that I cut with my Outline machine, holding the region under our kitchen sink coordinated
All we utilize these adorable plastic cabinet units to conceal Donnie’s shaving gear in our main restroom — they come in a wide range of tomfoolery tones!
Mint Stacking Drawers to Coordinate a Main Restroom Vanity
We additionally use stacking plastic capacity drawers to keep our pre-worn stuff coordinated, which makes it simple to change things out as the young men develop.
Plastic Stacking Stockpiling Drawers Used to Coordinate Pre-worn stuff
4. Plastic/Acrylic Stacking Storeroom Receptacles
At the point when we were first hitched, Donnie and I purchased a lot of economical storeroom containers, and they have been utilized for the vast majority, many purposes in the 10+ years since (they’re actually serious areas of strength for going over 10 years)!
They’re white, so they can fit in pretty much anyplace, and they’re likewise stackable, so we can undoubtedly coordinate upward. We’ve utilized these containers to hold the young men’s socks and underpants, shoes, toys in the carport, exercise hardware, supplies under the restroom sink, and we’ve even really involved them for storeroom capacity!
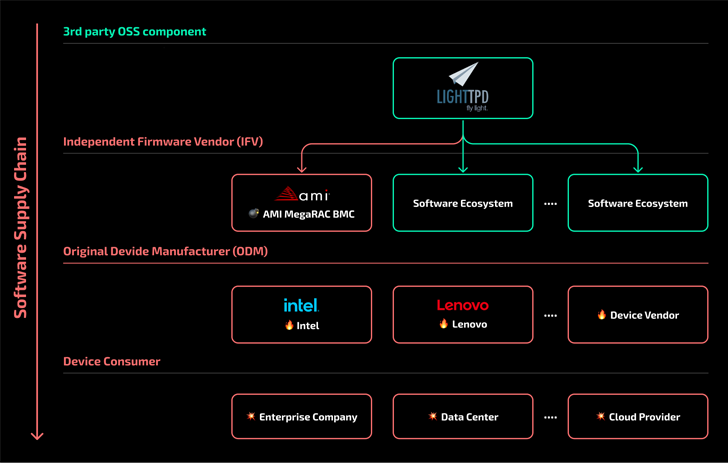
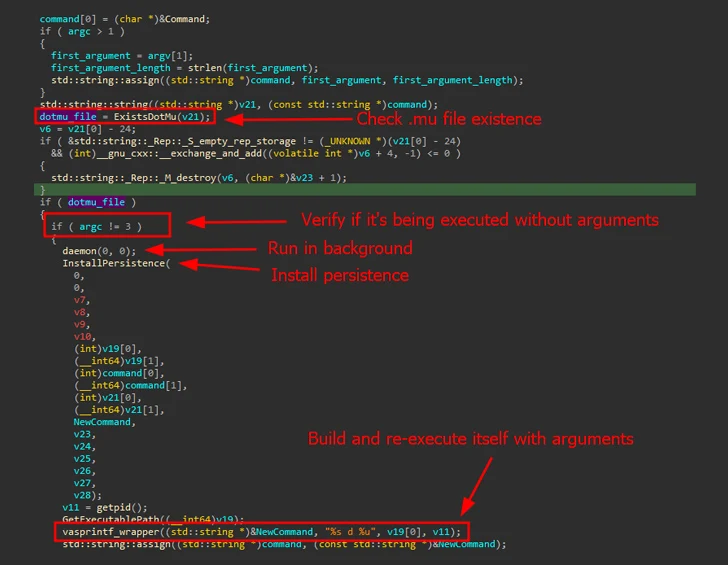
Intel and Lenovo BMCs Contain Unpatched Lighttpd Server Flaw
[ad_1]
A security flaw impacting the Lighttpd web server used in baseboard management controllers (BMCs) has remained unpatched by device vendors like Intel and Lenovo, new findings from Binarly reveal.
While the original shortcoming was discovered and patched by the Lighttpd maintainers way back in August 2018 with version 1.4.51, the lack of a CVE identifier or an advisory meant that it was overlooked by developers of AMI MegaRAC BMC, ultimately ending up in products made by Intel and Lenovo.
Lighttpd (pronounced “Lighty”) is an open-source high-performance web server software designed for speed, security, and flexibility, while optimized for high-performance environments without consuming a lot of system resources.
The silent fix for Lighttpd concerns an out-of-bounds read vulnerability that could be exploited to exfiltrate sensitive data, such as process memory addresses, thereby allowing threat actors to bypass crucial security mechanisms like address space layout randomization (ASLR).
“The absence of prompt and important information about security fixes prevents proper handling of these fixes down both the firmware and software supply chains,” the firmware security company said.
The flaws are described below –
- Out-of-bounds read in Lighttpd 1.4.45 used in Intel M70KLP series firmware
- Out-of-bounds read in Lighttpd 1.4.35 used in Lenovo BMC firmware
- Out-of-bounds read in Lighttpd before 1.4.51
Intel and Lenovo have opted not to address the issue as the products incorporating the susceptible version of Lighttpd have hit end-of-life (EoL) status and are no longer eligible for security updates, effectively turning it into a forever-day bug.
The disclosure highlights how the presence of outdated third-party components in the latest version of firmware can traverse the supply chain and pose unintended security risks for end users.
“This is yet another vulnerability that will remain unfixed forever in some products and will present high-impact risk to the industry for a very long time,” Binarly added.
[ad_2]
Source link
Google sues crypto investment app makers over alleged massive “pig butchering” scam
[ad_1]
Two China-based Android app developers are being sued by Google for an alleged scam targeting 100,000 users worldwide through fake cryptocurrency and other investment apps.
The company is taking action after scammers reportedly tricked victims with bogus promises of high returns from Android apps offering cryptocurrency investment opportunities.
At least 87 fake apps on Google Play promised returns to investors, but they could not access the claimed profits when they tried to withdraw funds.
Google alleges some fraud victims lost up to US $75,000.
According to Google, victims were asked to pay additional “fees” or “taxes” before a withdrawal, which the scammers would pocket.
Google sued two men, Yunfeng Sun (also known as “Alphonse Sun” and Hongnam Cheung (also known as “Zhang Hongnim” or “Stanford Fischer”) – are alleged to have committed “hundreds of acts of wire fraud.”
Google claims the men used three primary methods to “socially engineer and lure victim investors to download their fraudulent apps from Google Play and other sources”:
- Text messages would be sent via Google Voice to potential victims, disguised as messages sent to a wrong number (for instance, “I am Sophia, do you remember me?”). Conversations would be shifted to other platforms, and an attempt would be made to develop a friendship or romantic relationship that would ultimately try to persuade victims to invest via one of the apps (a technique known as “pig butchering”).
- Online videos tricked potential investors by presenting crypto apps as legitimate and safe. The videos would promise a high returns on investment and share details of a platform’s “leadership team” who were in fact paid actors.
- Affiliate marketing campaign that convinced users to become “affiliates” of investment apps with the promise that they would earn commission by signing up more users via social media to a “guaranteed and easy way to earn money.”
Bogus investment platforms like TrionRT appeared legitimate through a variety of methods, including distributing press releases.
When victims complained to the “friend” or “romantic partner” who had encouraged them to use the service, they would find that their “friend” or “romantic partner” had disappeared.
SkypeWallet, an allegedly fraudulent cryptocurrency investment app Google linked to Yunfeng Sun, was promoted with videos featuring the supposed leadership team of a company called SkypeCoin and guarantees high returns.

A similar promotional video exists for another reported fraud scheme, OTCAI.

Amusingly, both videos claim to show the company founder (“Romser Bennett”) but clearly feature different people played by different actors.
Furthermore, the actor playing an engineer called “Rodriguez” in the video for one app plays a technical leader named “William Bryant” for another.
The lawsuit by Google is the latest in a line of actions against fraudsters targeting Android users. Although it has removed offending apps from Google Play when discovered, the scammers are alleged to have created new aliases to disguise their connection to the apps.
[ad_2]
Source link
Linux Version of DinodasRAT Spotted in Cyber Attacks Across Several Countries
[ad_1]
A Linux version of a multi-platform backdoor called DinodasRAT has been detected in the wild targeting China, Taiwan, Turkey, and Uzbekistan, new findings from Kaspersky reveal.
DinodasRAT, also known as XDealer, is a C++-based malware that offers the ability to harvest a wide range of sensitive data from compromised hosts.
In October 2023, Slovak cybersecurity firm ESET revealed that a governmental entity in Guyana has been targeted as part of a cyber espionage campaign dubbed Operation Jacana to deploy the Windows version of the implant.
Then last week, Trend Micro detailed a threat activity cluster it tracks as Earth Krahang and which has shifted to using DinodasRAT since 2023 in its attacks aimed at several government entities worldwide.
The use of DinodasRAT has been attributed to various China-nexus threat actors, including LuoYu, once again reflecting the tool sharing prevalent among hacking crews identified as acting on behalf of the country.
Kaspersky said it discovered a Linux version of the malware (V10) in early October 2023. Evidence gathered so far shows that the first known variant (V7) dates back to 2021.
It’s mainly designed to target Red Hat-based distributions and Ubuntu Linux. Upon execution, it establishes persistence on the host by using SystemV or SystemD startup scripts and periodically contacts a remote server over TCP or UDP to fetch the commands to be run.
DinodasRAT is equipped to perform file operations, change command-and-control (C2) addresses, enumerate and terminate running processes, execute shell commands, download a new version of the backdoor, and even uninstall itself.
It also takes steps to evade detection by debugging and monitoring tools, and like its Windows counterpart, utilizes the Tiny Encryption Algorithm (TEA) to encrypt C2 communications.
“DinodasRAT’s primary use case is to gain and maintain access via Linux servers rather than reconnaissance,” Kaspersky said. “The backdoor is fully functional, granting the operator complete control over the infected machine, enabling data exfiltration and espionage.”
[ad_2]
Source link
AI’s role in innovation expanding rapidly
[ad_1]
SAN FRANCISCO — At times attendees of the Future Food Tech conference held March 21-22 in San Francisco may have been skeptical about the futuristic discussions taking place during the program and on the exhibit floor. At other times, it all came together and made sense. And even better – it made sense for right now.
“Foods have to be delicious and nutritious,” said Isabelle Esser, chief research and innovation, quality and food safety officer for Danone SA, Paris. “Technology needs scale and impact. It’s all about positive nutrition, and this requires collaboration.”
That’s much of what Elo Life Systems, Durham, NC, is striving to accomplish. Elo Life’s molecular farming platform produces ingredients that may be difficult to harvest from natural sources and may not be synthesized through artificial or other techniques. The company produces easy-to-grow crops as bio factories for the ingredients.
“We’re on a mission to unlock nature’s abilities to make consumers’ favorite foods more delicious, healthy and planet friendly,” said Todd Rands, chief executive officer of Elo Life Systems. “It’s about making foods more nutrient dense, not calorically dense, which has been the case with our food system since the second half of the 20th century.
“We use AI (artificial intelligence) and proprietary algorithms to gain deeper insights across native genomes, genes and traits. Innovation with healthy and sustainable food is desperately needed, and our collective future depends on creating new solutions that do not exist today.”
The company’s first product is a monk fruit-derived sweetener that will launch in 2026. Rands said the company is working on the production of varied bioactive ingredients and novel proteins.
Algorithms enable machines to learn and make decisions. Otherwise known as generative artificial intelligence, the technology is “transforming possibilities into reality,” said Lanette Shaffer Werner, chief innovation, technology and quality officer, General Mills, Minneapolis.
“For us, AI is a member of the team. It’s like having an intern on the team, who contributes like all other team players.” said Shaffer Werner. “AI provides input to our final decision. We still keep the consumer at the heart of everything we do.”
She explained how AI is an active player behind the scenes and how AI allows us “to have one eye on today and one on the horizon. For example, before a new product goes into test market, we can work with digital concepts generated by AI,” said Shaffer Werner.
Another valuable use for AI at General Mills is for a review of scientific literature. The company works with the program scite to get answers to all types of food innovation issues, everything from ingredients to food safety to yield.
“There are billions of scientific articles, many containing insight and solutions to issues we are facing,” Shaffer Werner said. “With AI, we can dedicate our resources to ‘doing’ instead of untangling pandora’s box.”
Brightseed, San Francisco, uses AI to discover bioactive compounds in nature and develop healthy food ingredients. The company served its newly launched bioactive fiber in yogurt parfaits at Future Food Tech.
The fiber ingredient was developed in partnership with Manitoba Harvest, Winnipeg, Man. It is a multi-benefit fiber solution developed from upcycled hump hulls. The product is unique for the fiber market as it has two phenolic bioactive compounds that research has shown may strengthen the gut lining to help maintain healthy gut barrier function.
“Bioactives are the unsung heroes of proactive health and today. The majority of people don’t consume enough to capture the full impact of their benefits,” said Sofia Elizondo, co-founder and chief operating officer of Brightseed. “Now that our AI Forager is powering the discovery and understanding of bioactives at an unprecedented rate, our mission at Brightseed is to transform those insights into accessible and powerful wellness products across the globe.”
Israel-based start-up Celleste-Bio uses a proprietary combination of biotechnology and AI to produce cocoa ingredients. Precision fermentation eliminates the dependence on cultivation of cocoa trees and will help ensure cocoa yield supply is invariable, not dependent on climate conditions, close to production sites and a final product of superior quality.
This is accomplished without genetic modification or manipulation by extracting cocoa cells from cocoa pods and growing them in a controlled setting with water and nutrients. It is a continuous cycle that repeats itself, without needing to crack open another pod.
“We want to offer people the pleasure and health that high-quality cocoa products provide, while eliminating the challenges of sustainable production that we face in cocoa production today,” said Hanne Volpin, co-founder and chief technology officer.
AI has helped Olipop, Oakland, Calif., grow its subscription platform by more than 35%. The company makes soda healthier, without necessarily broadcasting it, according to Olipop. While traditional soda has high levels of sugar, each can of Olipop contains 35 to 45 calories, 2 to 5 grams of natural sugars and 9 grams of prebiotic plant fiber.
“Americans have enjoyed soda for over 125 years. It has deep emotional and cultural resonance for consumers, and the category has become intertwined with our daily lives,” said Ben Goodwin, co-founder and CEO. “Our goal has always been to offer a product that can truly occupy the space that traditional soda has filled while also contributing to consumers’ overall well-being.”
Goodwin defended the concept of “ultra processing,” which has become the latest target in the food policing world. The reality is that the future of food depends on ultra processing.
“Ultra processing is necessary to make the fiber ingredient to get it into our beverage,” Goodwin said. “Rather than trying to tell consumers they can’t have soda, we are making it better for them. Olipop is more than ‘not harmful.’ It has a benefit.”
Providing a benefit in the form of sustainable practices also was a recurring theme at Future Food Tech. However, sustainability cannot be the No. 1 selling point, said Jack Bobo, director of the University of Nottingham’s Food Systems Institute in the United Kingdom. First comes taste, nutrition and price.
“Consumers don’t change their eating habits to save their lives. Why would they do so to save the planet?” Bobo said.
One Good Thing, Hertfordshire, England, believes it hits all the marks — taste, nutrition and price — with the extra plus of sustainability. The start-up has produced a range of wrapper-less oat and protein bars in a bid to reduce plastic waste for on-the-go snackers. Each bar is made from raw, cold-pressed ingredients coated with an edible beeswax film, that dries hard enough to hold and protect the contents but is thin and soft enough to chew easily.
The beeswax coating acts as a replacement to a traditional plastic or paper wrapper. Each bar is durable, and the packaging is waterproof. The only packaging is the cardboard boxes that the bars are delivered in, which is made of 70% recycled material and is 100% recyclable.
“The idea for One Good Thing came to me when I was out cycling and saw the sheer volume of snack wrappers. So, I challenged myself to think about how I could resolve the problem for people snacking on the go,” said Mike Bedford, founder. “We like to think of our bars as just like eating an apple. When you’re ready to eat one, you can just give it a quick rinse and pop it in. It’s that simple. Our innovation doesn’t just limit plastic waste. It removes it entirely.”
[ad_2]
Source link
Fujitsu hack raises questions, after firm confirms customer data breach • Graham Cluley
[ad_1]
Fujitsu has warned that cybercriminals may have stolen files with personal and customer data after it discovering malware on its computer systems.
The firm at the center of the British Post Office scandal, said in a Japanese press release that it had discovered the presence of malware on its computers, the potential theft of customer data, and apologised for any concern or inconvenience caused.
The press release (a Google-translated version can be read here), is somewhat scant on detail.
For instance:
- Fujitsu doesn’t disclose the malware found, the number of affected computers, or the internal systems or databases accessed.
- Fujitsu doesn’t specify the type of malware found – a remote access backdoor? ransomware? something else?
- Fujitsu doesn’t share details about the stolen information, calling it “personal information and customer information.” For instance, does it include contact details, passwords, or payment information?
- Fujitsu announced on Friday 15 March that it suffered a cyber attack, but didn’t specify when it was discovered or how long the hackers had access to its systems and data.
Fujitsu says it has reported the incident to regulators and will contact affected individuals and customers.
The company also says that it has not seen any reports of the potentially stolen information being misused. Statements like these are meant to reassure affected parties, but they don’t make you feel much more comfortable in reality.
An absence of evidence is not evidence of absence. How could a company ever confidently and honestly claim it has incontrovertible proof that exfiltrated data has not been exploited by malicious hackers and online fraudsters?
In the past, there have been many incidents where data stolen in a hack has not immediately shown up, before appearing on the dark web months or even years later.
[ad_2]
Source link
Microsoft Confirms Russian Hackers Stole Source Code, Some Customer Secrets
[ad_1]
Microsoft on Friday revealed that the Kremlin-backed threat actor known as Midnight Blizzard (aka APT29 or Cozy Bear) managed to gain access to some of its source code repositories and internal systems following a hack that came to light in January 2024.
“In recent weeks, we have seen evidence that Midnight Blizzard is using information initially exfiltrated from our corporate email systems to gain, or attempt to gain, unauthorized access,” the tech giant said.
“This has included access to some of the company’s source code repositories and internal systems. To date we have found no evidence that Microsoft-hosted customer-facing systems have been compromised.”
Redmond, which is continuing to investigate the extent of the breach, said the Russian state-sponsored threat actor is attempting to leverage the different types of secrets it found, including those that were shared between customers and Microsoft in email.
It, however, did not disclose what these secrets were or the scale of the compromise, although it said it has directly reached out to impacted customers. It’s not clear what source code was accessed.
Stating that it has increased in its security investments, Microsoft further noted that the adversary ramped up its password spray attacks by as much as 10-fold in February, compared to the “already large volume” observed in January.
“Midnight Blizzard’s ongoing attack is characterized by a sustained, significant commitment of the threat actor’s resources, coordination, and focus,” it said.
“It may be using the information it has obtained to accumulate a picture of areas to attack and enhance its ability to do so. This reflects what has become more broadly an unprecedented global threat landscape, especially in terms of sophisticated nation-state attacks.”
The Microsoft breach is said to have taken place in November 2023, with Midnight Blizzard employing a password spray attack to successfully infiltrate a legacy, non-production test tenant account that did not have multi-factor authentication (MFA) enabled.
The tech giant, in late January, revealed that APT29 had targeted other organizations by taking advantage of a diverse set of initial access methods ranging from stolen credentials to supply chain attacks.
Midnight Blizzard is considered part of Russia’s Foreign Intelligence Service (SVR). Active since at least 2008, the threat actor is one of the most prolific and sophisticated hacking groups, compromising high-profile targets such as SolarWinds.
[ad_2]
Source link
Someone is hacking 3D printers to warn owners of a security flaw
[ad_1]
Do you have an Anycubic Kobra 2 Pro/Plus/Max 3D printer? Did you know it has a security vulnerability?
If you answered “yes” to both those questions, then chances are that I can guess just how you found out your 3D printer was vulnerable to hackers.
My bet is that you might have learnt about the problem after seeing a strange message displayed on your device, claiming that it had been hacked.
As multiple posts on Reddit confirm, owners of the 3D printers have had an unusual message pop up on their devices.
The message contains ASCII art of a worm and claims to be “harmless” – but warns of a “critical vulnerability” in the printer, posing a “significant threat”. It advises affected users to disconnect their printer from the internet to avoid being hacked.
In the message, someone calling themselves “printer god” bemoans Anycubic’s lax security and warns that a malicious attack could have caused damage.
The warning message in the file hacked_machine_readme.gcode can be safely deleted from the printer’s screen or USB drive. The author claims to have sent it to over 2.9 million vulnerable printers.
The hack seems to be connected to a post in an online forum earlier this week by a user called “Dump”. “Dump” claimed to have tried to communicate with Anycubic for two months about “two critical security vulnerabilities” – with one described as “catastrophic if found to be malicious.”
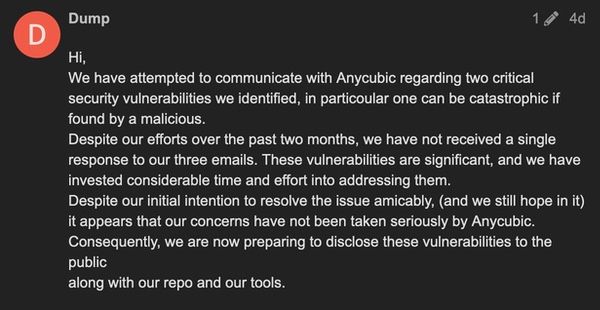
Anycubic has now confirmed the existence of a “security issue”, which it claims was “caused by a third party using a security vulnerability of the MQTT server to access users’ printers.”
Anycubic says that it is enhancing its cloud server security and will release new firmware to users on March 5, 2024.
This isn’t the first time that printers have been hijacked through security vulnerabilities to spread messages. For instance, in 2018, thousands of printers were seized to print out a message promoting PewDiePie’s YouTube channel.
[ad_2]
Source link
Texture innovation: ‘Air is the ingredient of the future’
[ad_1]
CHICAGO — Texture is something one does not think about when eating, unless it’s off. It’s an attribute that is more than mouthfeel and incorporates how food dissolves in the mouth and how it’s tasted. It’s the third dimension and is mostly about nothing. But nothing is something.
Ice cream manufacturers have long understood the role air plays in texture development. They refer to the amount of air incorporated into mix prior to freezing as overrun. The less overrun, the more dense the ice cream; and often the more expensive. After all, air is free.
“Texture is the next thing,” said Morgaine Gaye, a global food futurologist based in the UK. “It’s not just the surface anymore.”
Consumers often think they taste texture but in reality texture is a flavorless attribute. It is, however, the backbone of food product development because it has an impact on the other attributes.
“We believe texture plays an underappreciated but critical role in how consumers like or don’t like the food they eat,” said James P. Zallie, president and chief executive officer, Ingredion Inc., Westchester, Ill., during a Feb. 21 presentation at the Consumer Analyst Group of New York conference.
So why texture now? As a food futurologist, Gaye is in tune with general pop culture, everything from fashion to geopolitics.
“And right now, with everything going on in the world, consumers do not want to be tied down,” she said. “People are off-loading. They want less. They crave a feeling of lightness, and that’s what you get with air.”
Think lattice cookies, marshmallows and cream cheese. With the latter, note how the texture varies between a block and whipped tub. Crevices and pockets create unique textures and thus, eating experiences. Manufacturing processes may assist with incorporating air and water.
Ingredients also play a role. Think how gluten entraps air in a leavened baked food and how gelatin turns water into a slick, melt-in-your-mouth encounter.
Gaye believes 3D-printing will play an important role in developing new textures in foods.
“Air creates interest,” she said. “Air is the ingredient of the future.”
Texture is something ingredient companies have been trying to emphasize as a way of creating a point of differentiation in the marketplace. Texturants are a category of ingredients that assist with incorporating air or binding water in a food matrix.
Usually carbohydrate or protein based, texturants vary in function and by application. For example, maltodextrins and polydextrose add body and build total solids, while starches add viscosity and body. Gums tend to build viscosity and prevent phase separation, while emulsifiers bind fat and aqueous phases.
Zallie said the market for texturizing ingredients is “a large addressable market that is growing steadily.”
He said the Ingredion’s market insights group found superior texture for taste is foundational for consumer preference. In fact, 70% of consumers agreed texture gave foods and beverages a more interesting eating experience, according to consumer research conducted by the company.
“Think for a moment about boba tea, which has gained popularity and contains tapioca pearls, which is basically tapioca starch and some hydrocolloids to keep the product to have its integrity in a beverage,” Zallie said. “And 84% of consumers associated a lighter texture with healthier options. Think rice cakes or rice crisps, for example.”
Product developers should address texture needs first in order to make sure the ingredients used in the formulation stand up to the manufacturing process and storage requirement conditions. Once that is confirmed, then flavor, color and the other attributes may be addressed.
[ad_2]
Source link
New Wi-Fi Vulnerabilities Expose Android and Linux Devices to Hackers
[ad_1]
Cybersecurity researchers have identified two authentication bypass flaws in open-source Wi-Fi software found in Android, Linux, and ChromeOS devices that could trick users into joining a malicious clone of a legitimate network or allow an attacker to join a trusted network without a password.
The vulnerabilities, tracked as CVE-2023-52160 and CVE-2023-52161, have been discovered following a security evaluation of wpa_supplicant and Intel’s iNet Wireless Daemon (IWD), respectively.
The flaws “allow attackers to trick victims into connecting to malicious clones of trusted networks and intercept their traffic, and join otherwise secure networks without needing the password,” Top10VPN said in a new research conducted in collaboration with Mathy Vanhoef, who has previously uncovered Wi-Fi attacks like KRACK, DragonBlood, and TunnelCrack.
CVE-2023-52161, in particular, permits an adversary to gain unauthorized access to a protected Wi-Fi network, exposing existing users and devices to potential attacks such as malware infections, data theft, and business email compromise (BEC). It impacts IWD versions 2.12 and lower.
On the other hand, CVE-2023-52160 affects wpa_supplicant versions 2.10 and prior. It’s also the more pressing of the two flaws owing to the fact that it’s the default software used in Android devices to handle login requests to wireless networks.
That said, it only impacts Wi-Fi clients that aren’t properly configured to verify the certificate of the authentication server. CVE-2023-52161, however, affects any network that uses a Linux device as a wireless access point (WAP).
Successful exploitation of CVE-2023-52160 banks on the prerequisite that the attacker is in possession of the SSID of a Wi-Fi network to which the victim has previously connected. It also requires the threat actor to be in physical proximity to the victim.
“One possible such scenario might be where an attacker walks around a company’s building scanning for networks before targeting an employee leaving the office,” the researchers said.
Major Linux distributions such as Debian (1, 2), Red Hat (1), SUSE (1, 2), and Ubuntu (1, 2) have released advisories for the two flaws. The wpa_supplicant issue has also been addressed in ChromeOS from versions 118 and later, but fixes for Android are yet to be made available.
“In the meantime, it’s critical, therefore, that Android users manually configure the CA certificate of any saved enterprise networks to prevent the attack,” Top10VPN said.
[ad_2]
Source link
Online Music Mastering Using Professionals
The crowning touch to any music track is its mastering, and in the age of the internet, access to professional services has never been more convenient. Achieving commercial-quality music mastering London is now within reach for everyone, thanks to a plethora of online experts proficient in handling the engineering and mixing of compositions, be it a single track or an entire CD. The depth and richness of sound attainable through proper digital mastering are not just desirable but have become an expected standard in today’s music publishing landscape.
While for initial samples, DIY mastering may suffice, stepping into the competitive real-world music industry demands the involvement of a professional mastering engineer. A subpar master can lead to rejection, branding a music track as amateurish solely due to defective sound quality.
Elevating Your Music to Commercial Quality
It is paramount to enlist the services of a professional who can guide the client through every facet of the sonic elements processing that comprises the tracks destined for distribution. Opting for an online expert operating from a modern music mastering studio space offers the convenience of an accessible platform for communication and feedback throughout the mastering process. Clients can convey their specific preferences using order or feedback forms, and engage in direct communication with the engineer via phone, chat, or other means while the job is in progress.
The collaborative relationship between the mastering engineer and the client ensures that the final product aligns with the artist’s vision, meets industry standards, and stands out in the competitive music market. By leveraging the expertise of online professionals, musicians can navigate the complexities of mastering and present their compositions in a way that captivates audiences, leaving a lasting impression of sonic excellence.